Hacker101 CTF: Micro-CMS v1 Writeup
A couple of days ago, I created an account on HackerOne to start my bug bounty journey. They have a ton of resources for newbies, including a whopping 26 CTF challenges at ctf.hacker101.com!
This is my writeup for the “Micro-CMS v1” challenge. Each flag is presented in the order that I found them.
Challenge Link: https://ctf.hacker101.com/ctf
Below is a screenshot of the website’s landing page:
I clicked on the first link title “Testing”. Take note of the page number in the URL for later on.
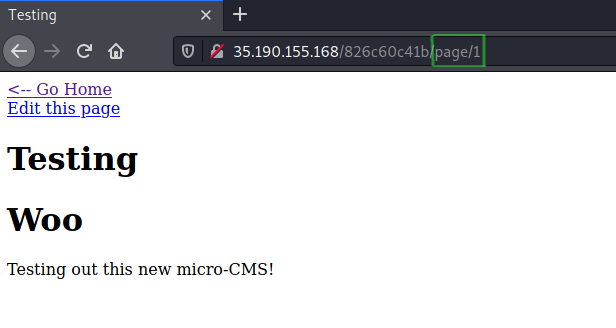
Flag0 – Stored XSS
Click on the “Edit Page” option. You should now see two input boxes for the title and body contents. Time to see what happens when we use an HTML script tag to inject JavaScript.
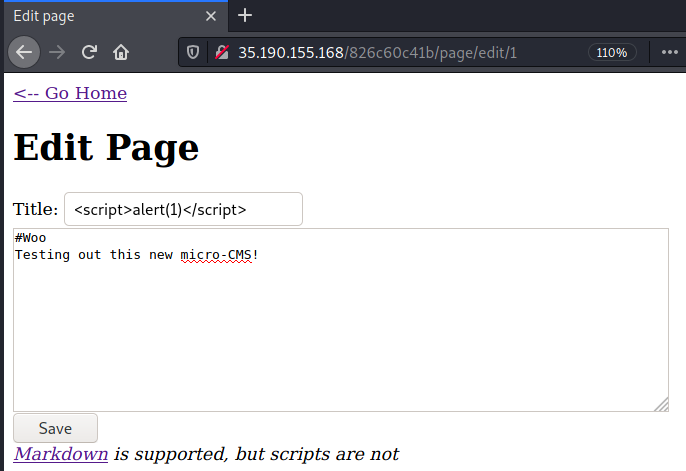
Above, I replaced “Testing” with <script>alert(1)</script>. When navigating
back to the home page, the flag pops up!

Note: The title section in Page 2 “Markdown Test” is also vulnerable to XSS injection.
Flag1 – 403 Forbidden Access
I discovered the next flag when creating a new page. Notice the page number in the URL.
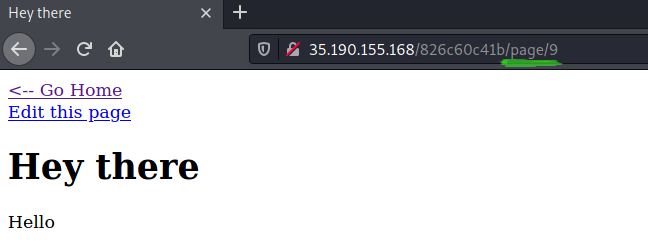
That’s odd that my page was assigned the number 9 instead of 3, which is the next sequential number after the two default pages.
I poked around and tried to visit http://35.190.155.168/826c60c41b/page/3, but got a Not Found
error.
This error happens on pages 3-8 except for page 4. That page gives us the following error:
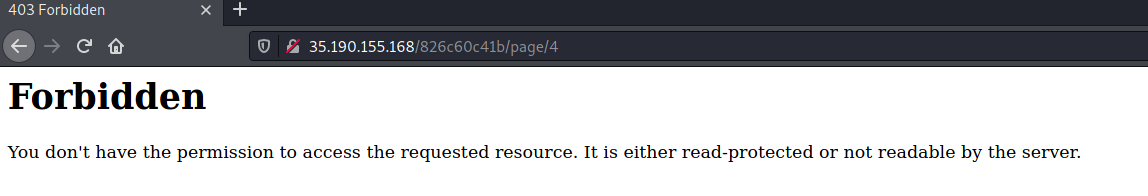
Hmmm. If the page cannot be access here, perhaps it can be accessed if we
go to http://35.190.155.168/826c60c41b/page/edit/4?
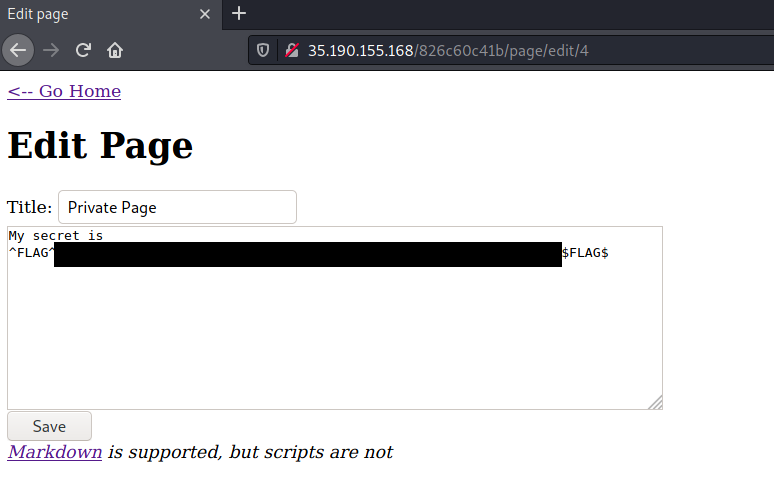
Bingo! Another flag!
Flag2 – SQLi
The next flag can be found with a very simple SQL Injection (SQLi). Navigate to any page, and click the “Edit this page” link. Insert a single quote (’) and witness the flag appear!
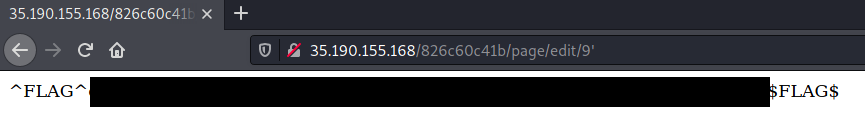
Flag3 – Stored XSS Again
The final flag can be found with another XSS attack. Edit an existing page or create a new one. For the first XSS attack, we injected code into the Title input box. This time around, we need to inject code into the body.
However, it looks like the body input box has a more advanced filter, as
a normal <script>alert(1)</script> tag will not work.
To find an alternative XSS attack, I used the XSS Filter Evasion Cheat Sheet from OWASP.
The below worked for me:
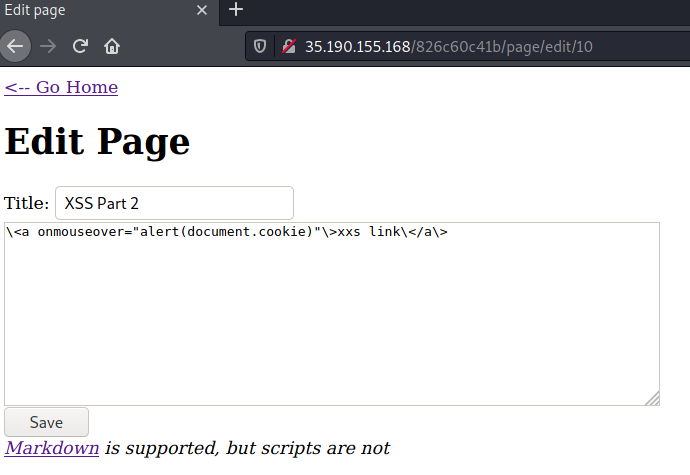
Press Save to reveal the flag!

Thanks for reading! If you enjoyed this post, consider sharing.