Tips for Learning Assembly Programming
Understanding an assembly language is a mandatory prerequisite skill for reverse engineering and binary exploitation. However, assembly languages can be intimidating for a beginner. In this post, I will share 3 tips to get better at reads, understanding and programming in assembly.
I also covered this topic in a YouTube video. Check it out!
Tip 1 - Overcoming Intimidation
Many individuals interested in low-level hacking, such as reverse engineering, game hacking, or exploit writing, may find Assembly Language intimidating.
It’s essential to understand that Assembly Language is not as scary as it seems. Different assembly languages may have varying numbers of instructions, but they can be categorized into common instruction types.
Breaking down instructions into types, such as assignment, arithmetic, stack manipulation, addressing, jumps, conditionals, and bitwise operations, helps reduce the perceived complexity.
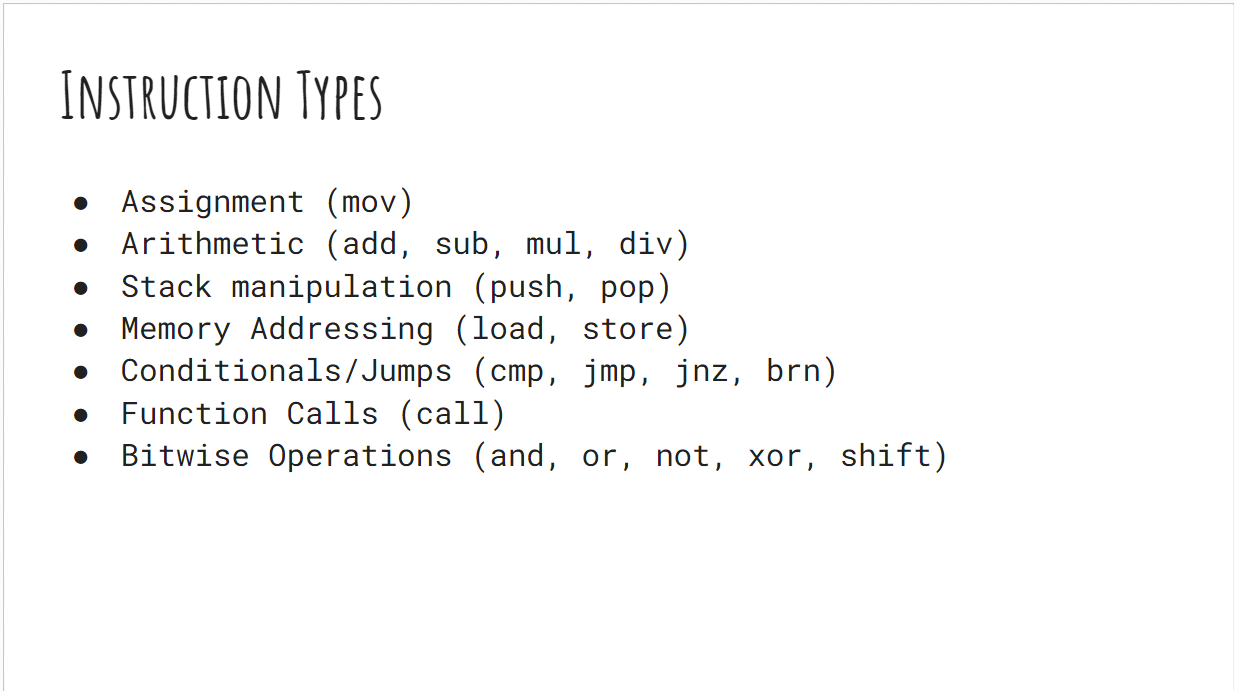
And for reverse engineering CTFs challenges, we can usually focus our attention on jump, cmp and call instructions to get an
understanding of the binary.
Tip 2 - Reading Documentation
Reading the documentation is crucial when dealing with Assembly Language, regardless of the specific language (e.g., ARM, x64, MIPS).
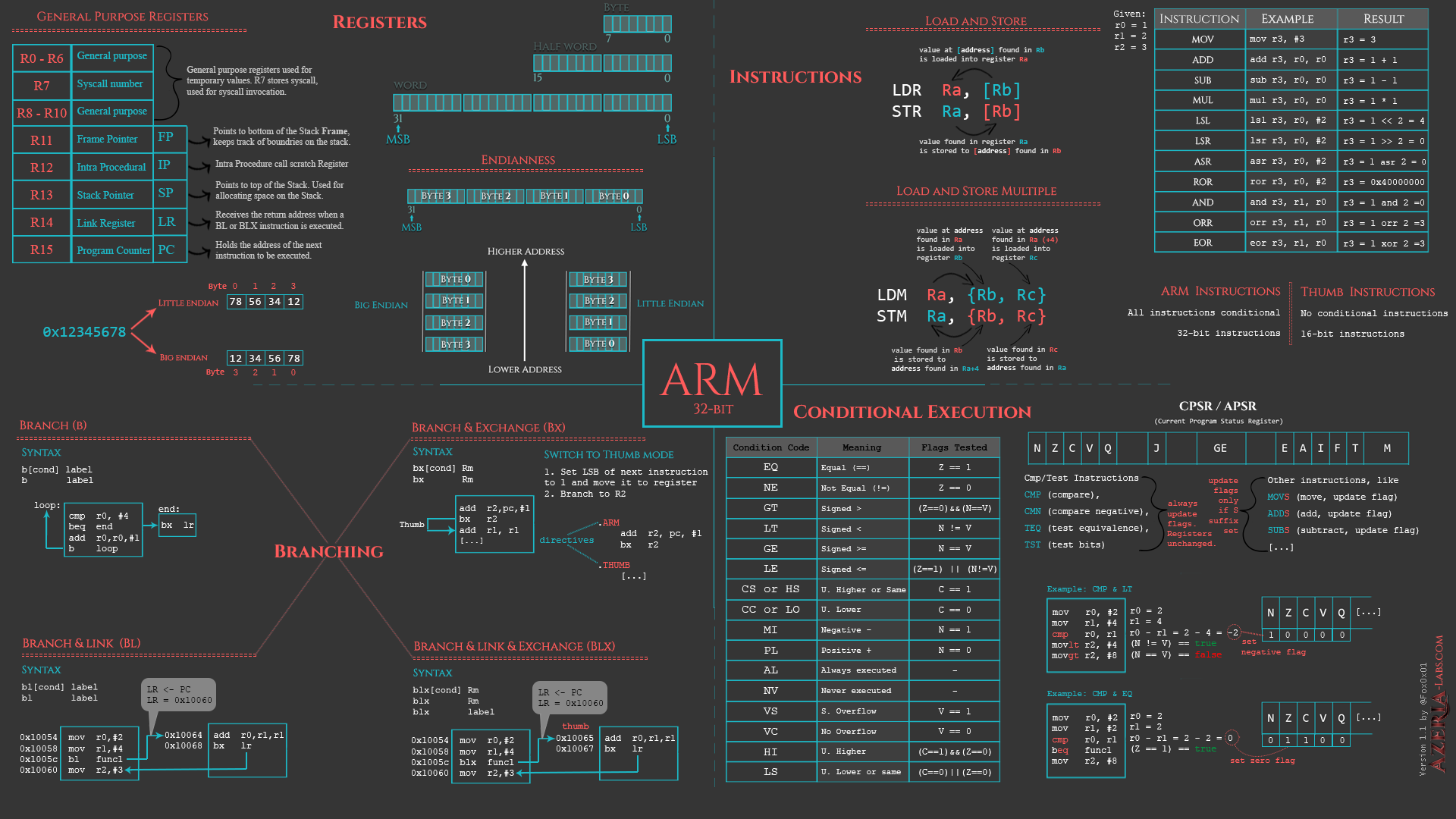
Utilizing reputable resources like Azeria Labs for ARM or Intel’s developer manuals for x64 can provide well-structured tutorials, cheat sheets, and detailed information on assembly instructions.
🔥 Check out these fantastic ARM assembly cheatsheets from Azeria Labs (@Fox0x01 on Twitter)
Link: https://azeria-labs.com/assembly-basics-cheatsheet/
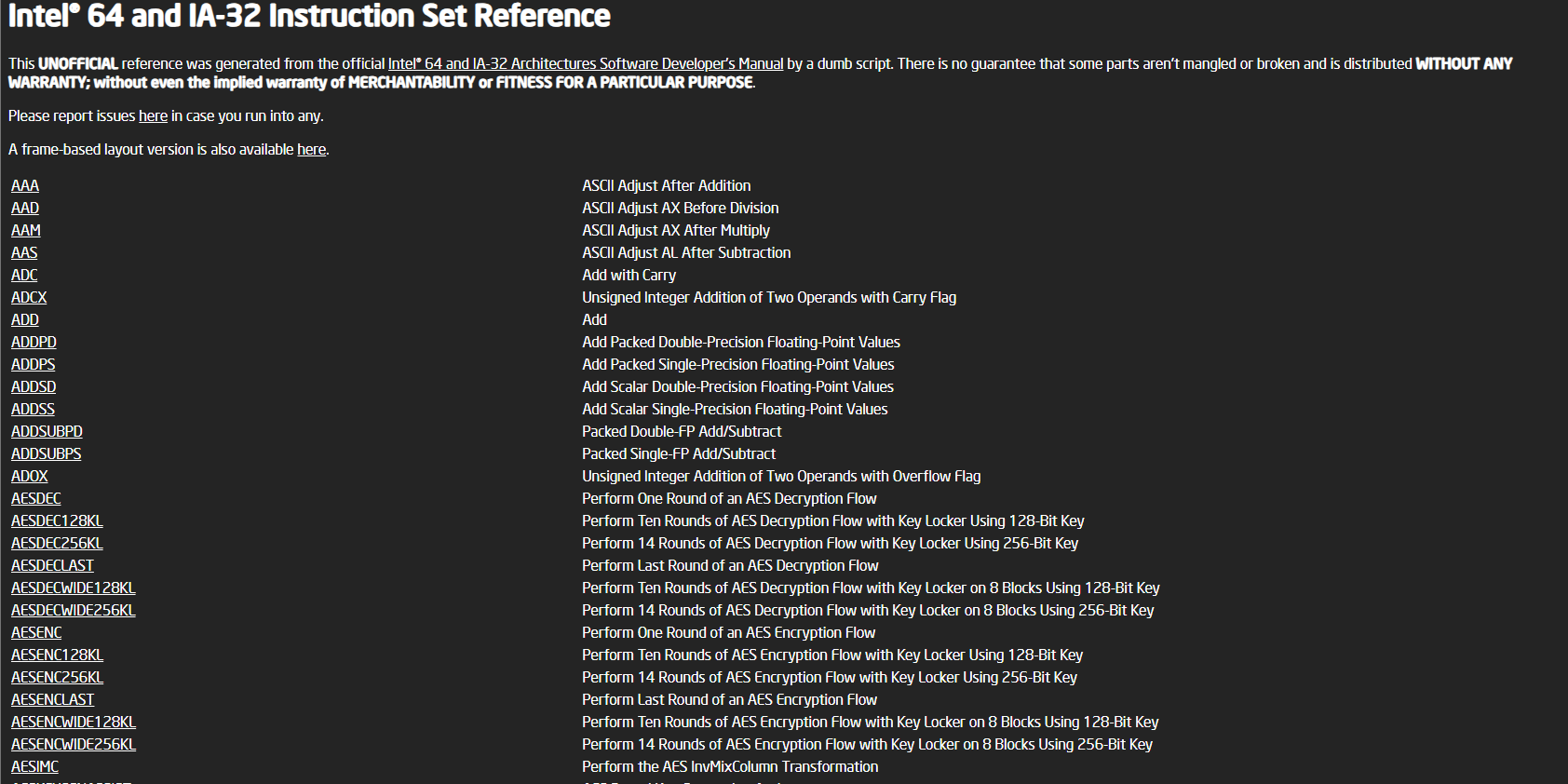
For Intel x64 and x86 instruction documentation, I really love the unofficial reference from namazso.
Link: https://namazso.github.io/x86/
Tip 3 - Read and Write Assembly Code
Practicing is crucial for becoming proficient in assembly language. During my undergraduate computer architecture course, we had lab assignments that involved translating C code to MIPS assembly… on paper! No computer tools or compilers were allowed for these assignments, essentially, we had to become the compiler.
As painful fun as those assignments were, I did in fact become better at programming in assembly and understanding how pointers
and arrays actually work under-the-hood in C.
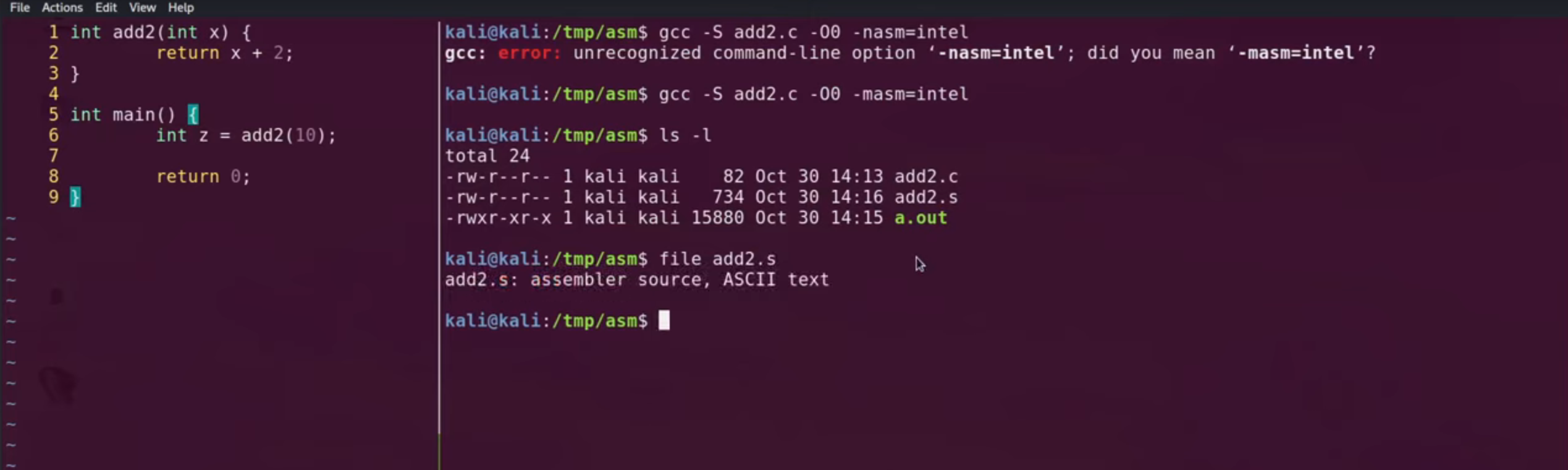
I am not ask you to translate your code on paper. There are great tools like the Godbolt Compiler Explorer to translate high-level languages (e.g., C, Python) to your assembly of choice.
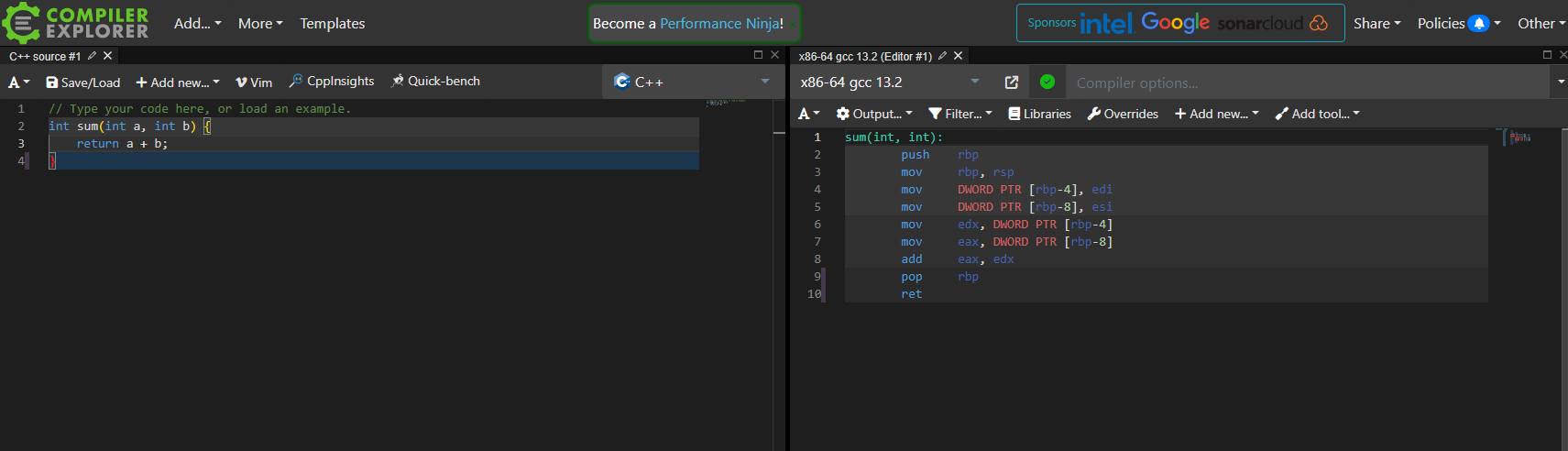
You can also write your own toy C programs and view the assembly output by running gcc -S myfile.c.
I walkthrough how to do this at the 9:14 mark of my video: https://youtu.be/tKGYU5wQCSA?si=uc11Yn6xlm1HK7SY&t=554
Conclusion
Hopefully these short blog post on tips help! It is not necessary to write/program in assembly language to do reverse engineering or binary exploitation. However, it can be a fun exercise to solidify some of the concepts and instructions.
If you have any questions feel free to reach out to me on Twitter or LinkedIn!
~happy hacking :)